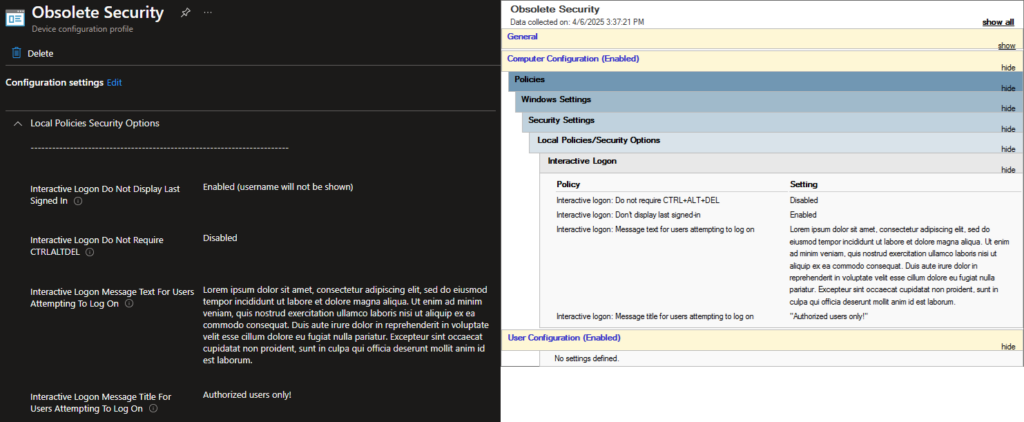
The settings in the above screenshots were fairly common to be applied to all workstations as a requirement 20-ish years ago. However, it’s now 2025, and we really don’t need to be setting them anymore, for multiple reasons. Let’s talk about it, or just jump to the TL;DR!
Interactive logon: Do not require CTRL+ALT+DEL
Requiring Ctrl+Alt+Del to sign in was a good security practice for Windows operating systems that did not have User Account Control (UAC). So we’re talking pre-Vista here. These operating systems did not have the enhanced security that UAC and the newer Winlogin process that were introduced with Vista and continuously enhanced with each later release.
Ctrl+Alt+Del is a “system interrupt” in Windows, that only the OS can respond to. For non-NT based Windows operating systems (3.x/9x), this would open something similar to Task Manager, and pressing it a second time would soft reboot the system. For NT-based Windows operating systems, this key combination would be intercepted by the logon process when at the logon screen, potentially preventing any malware that attempted to hijack the logon screen to steal credentials.
This enhancement is no longer necessary on modern Windows operating systems, thanks to multiple features such as UAC, driver signing, virtualization-based security, etc. It’s also just a nuisance for users to do in order to log in to their computer, especially with touchscreen devices or when using Windows Hello for Business.
Interactive logon: Don’t display last signed-in
This one is simple. It was mostly enabled to provide a false sense of security, where if a device was stolen, an attacker didn’t also have a username to attack. However, it again just becomes a nuisance to users, especially when using Windows Hello for Business, as they will now need to enter their username and select WHfB to sign in, instead of the ease of opening a laptop lid and face sign in instantly logging them in without doing anything.
Note: I’d still likely set this on shared devices, as it makes sense there, to help prevent users locking each other out. Shocked Pikachu face, users won’t realize their username isn’t in the username field.
Interactive logon: Message title/text for users attempting to log on
This one is also simple. It was thought to be a legal requirement, and still is by some. However, all employees should have signed an Acceptable Use Policy (AUP) or something similar when hired, well before they even touch a corporate-owned device. This document would likely contain anything and everything you could possibility put in the logon banner, and is more of a “legally binding” agreement than the logon banner is.
Logon banners will also cause issues with Autopilot provisioning, and again, can be a nuisance for users to click through (without reading of course), especially on touchscreen devices. They also again break the seamlesss flow of using WHfB to log in.
TL;DR
- Ctrl+Alt+Del to log in provides zero value on modern Windows operating systems thanks to other security mitigations/enhancements such as UAC, VBS, etc.
- Not displaying the last signed-in user provides zero value, breaks the Windows Hello for Business login flow, and is a nuisance to users
- Logon banners are not a replacement for requiring Acceptable Use Policies (AUPs) to be signed as part of the terms and conditions of employment, can break the Autopilot provisioning process, and users don’t read them anyway.
More Stuff!
Want to read more about other stuff you may want to reconsider? Check out my buddy Martin’s post about BitLocker PINs!



One thought on “Obsolete Security – Stop Setting These Policies!”