This post is mostly sourced from https://techcommunity.microsoft.com/t5/itops-talk-blog/step-by-step-migrating-active-directory-certificate-service-from/ba-p/2328766, along with some helpful notes, screenshots, and code samples from my own experience. It’s mostly here for my own documentation purposes.
Backup the CA
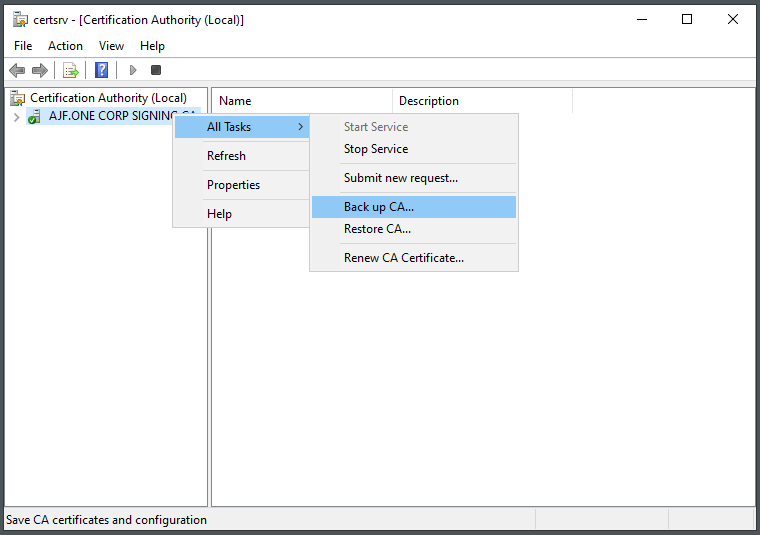
Select backup options
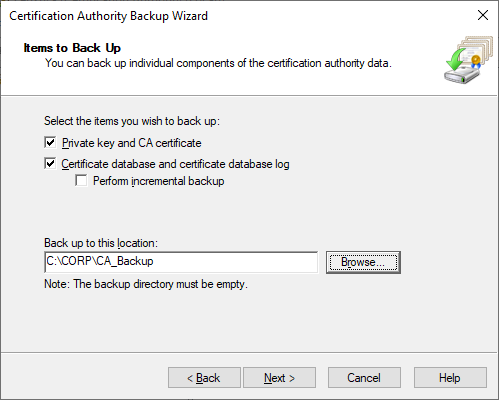
Generate and save a secure password
Click Finish
Export CA Registry Settings
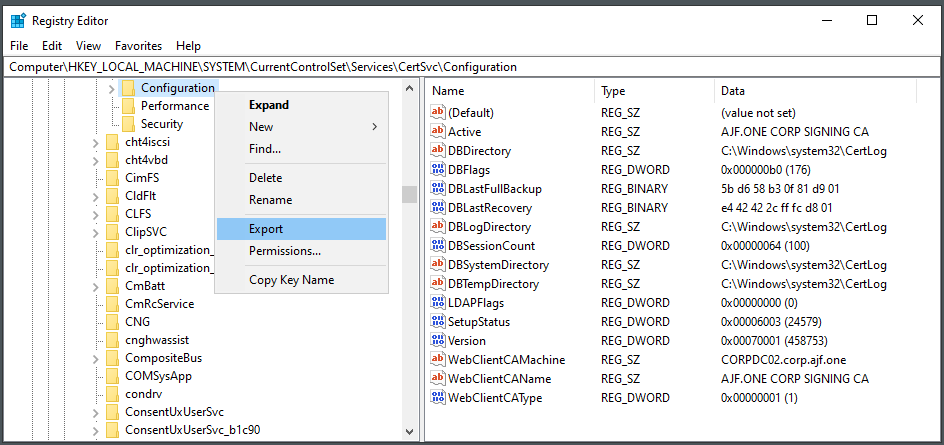
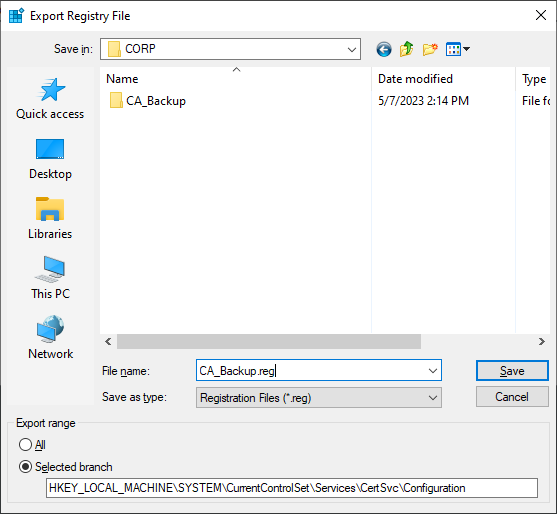
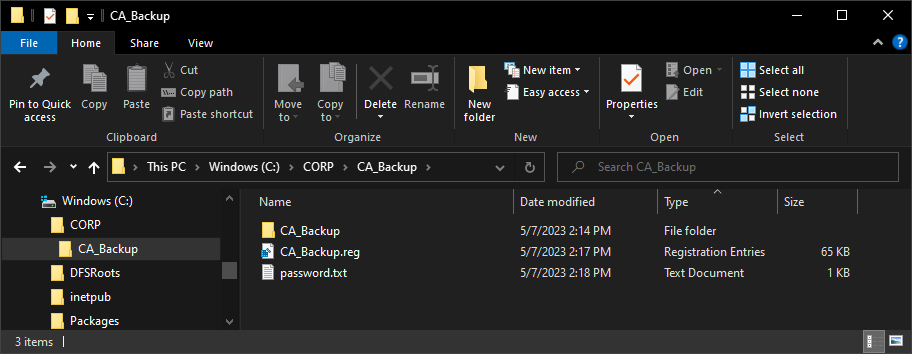
Copy the backup files to the new server
Uninstall ADCS roles and restart the server
Remove-WindowsFeature -Name ADCS-Web-Enrollment -Confirm:$false
Remove-WindowsFeature -Name ADCS-Online-Cert -Confirm:$false
Remove-WindowsFeature -Name ADCS-Cert-Authority -Confirm:$false
Restart-ComputerMove alternative name (if in use) from old server to new server
netdom computername OLDCA.ad.domain.tld /remove PKI.ad.domain.tldnetdom computername NEWCA.ad.domain.tld /add PKI.ad.domain.tld
ipconfig /registerdnsInstall AD CS Roles on New Server
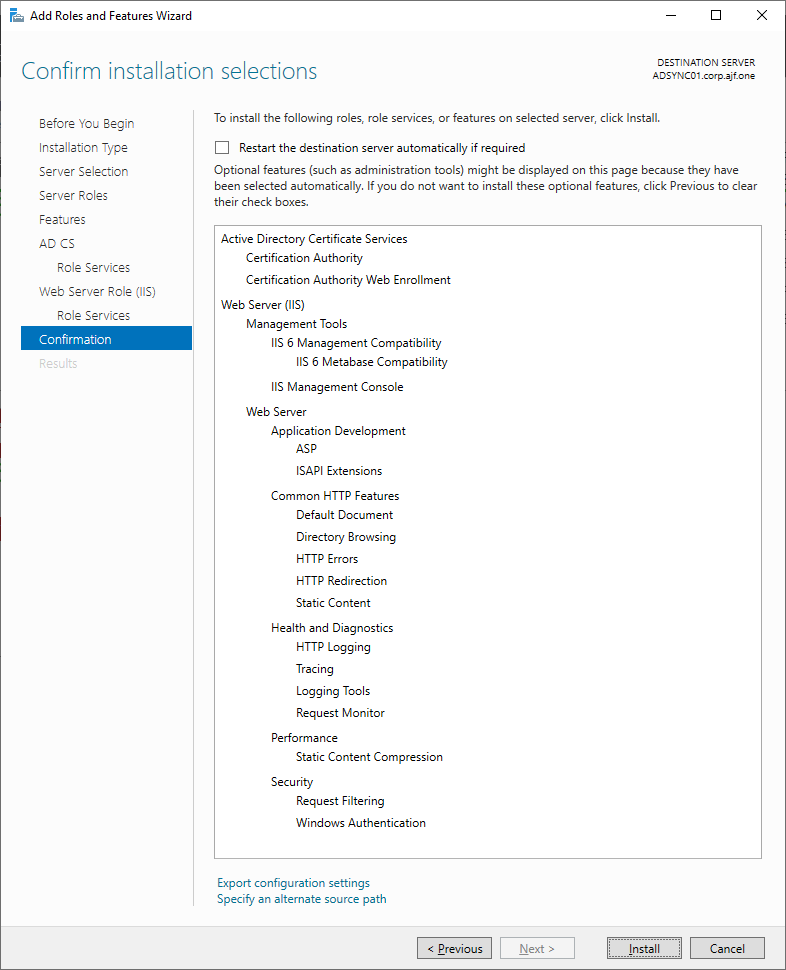
Configure the CA (remember to log in with Enterprise Admin credentials)
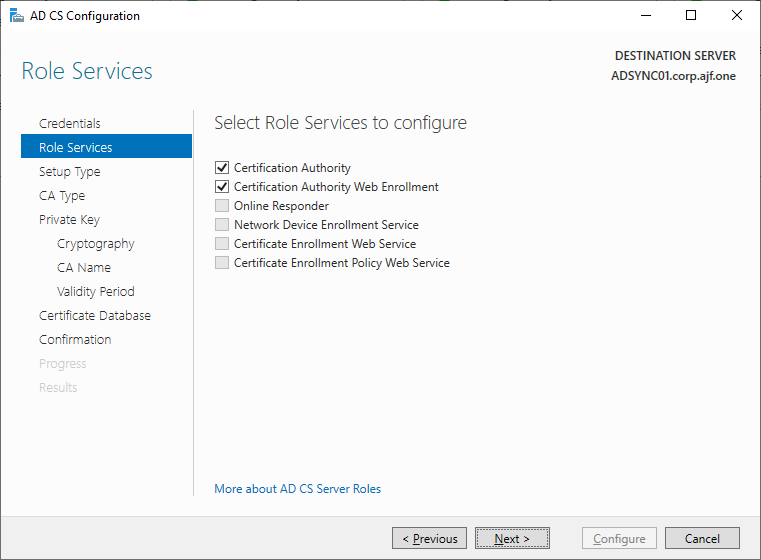
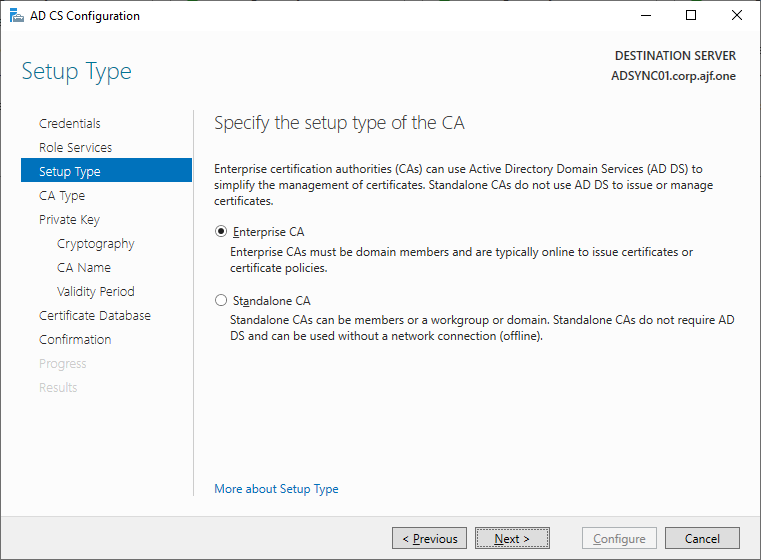
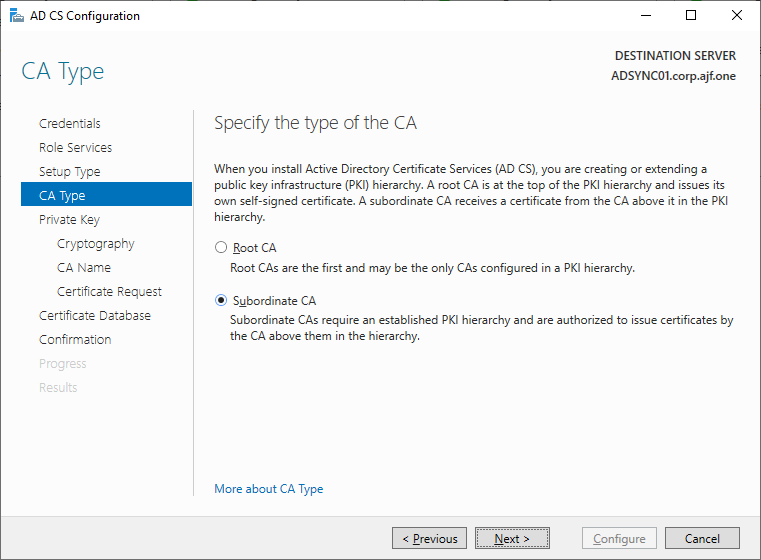
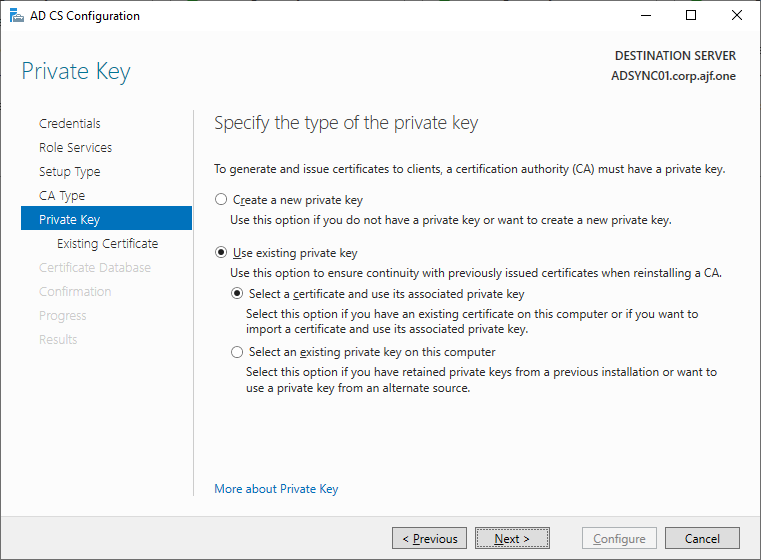
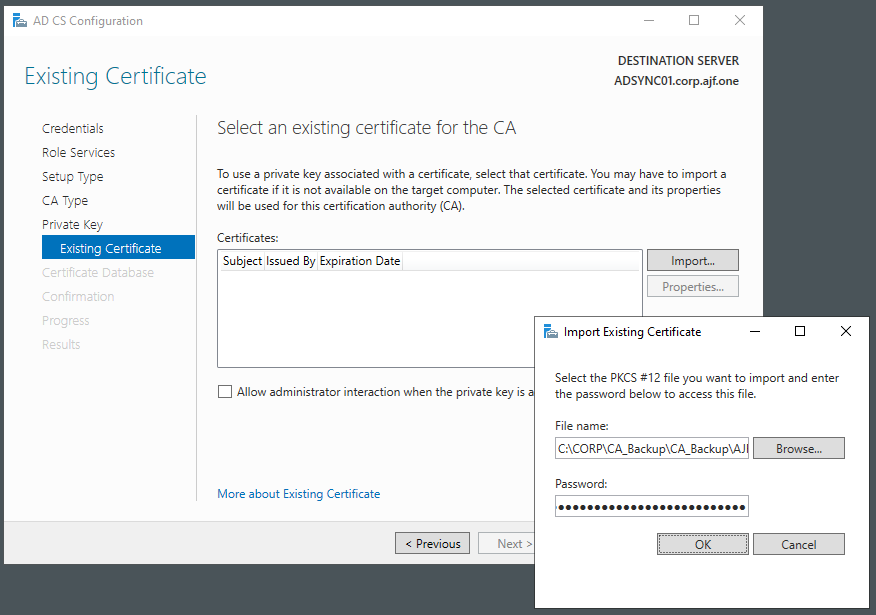
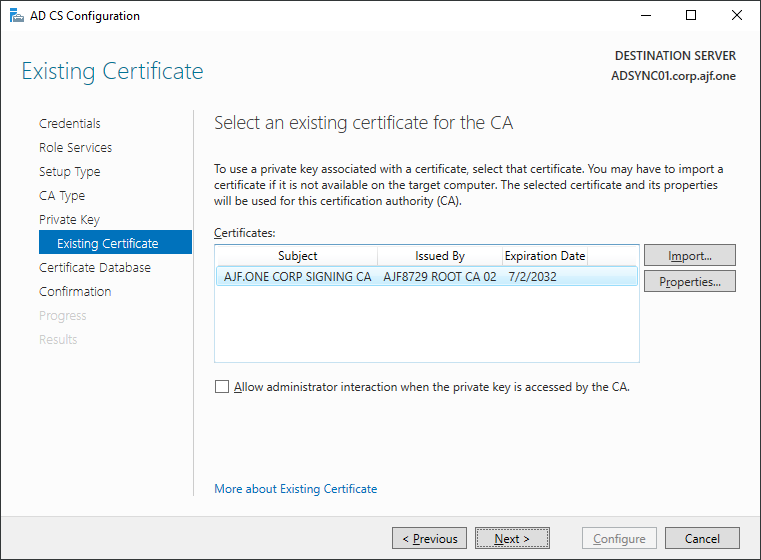
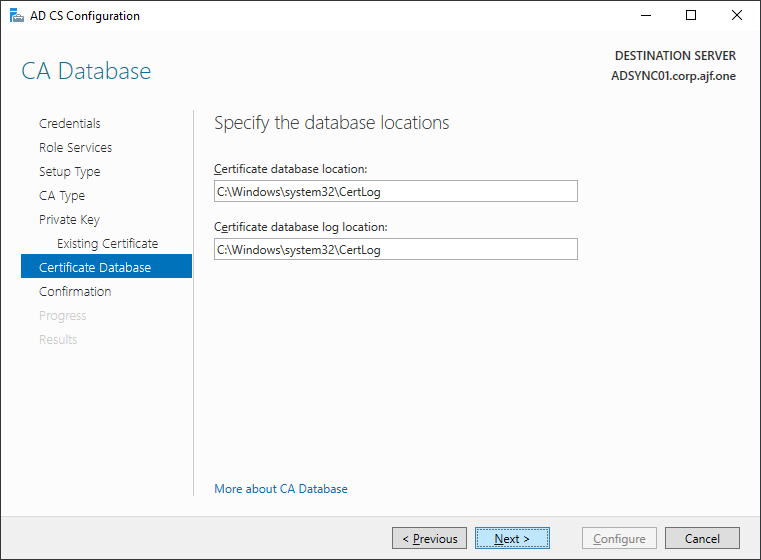
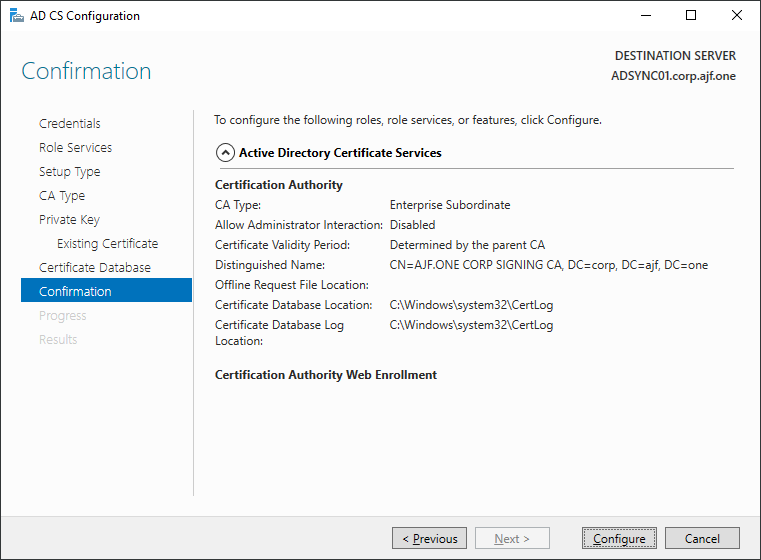
Restoring the CA Backup
Stop the CA service
Stop-Service -Name CertSvcEdit the registry backup and update the WebClientCAMachine and CAServerName values
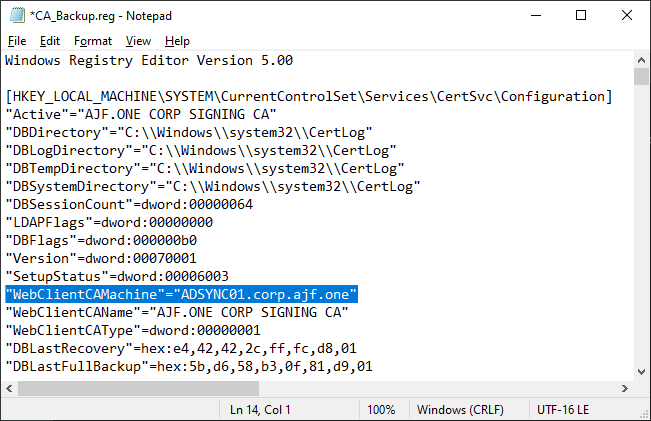
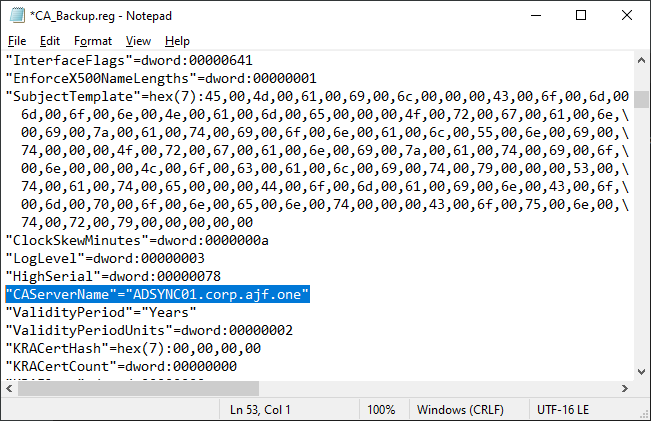
Restore the CA backup
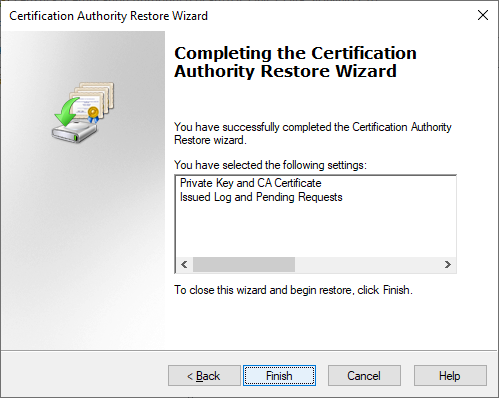
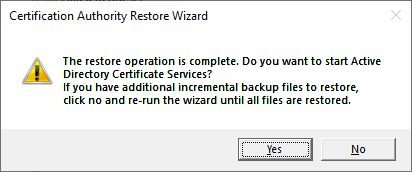
Import the registry backup, and restart ADCS again
reg import .\CA_Backup.reg
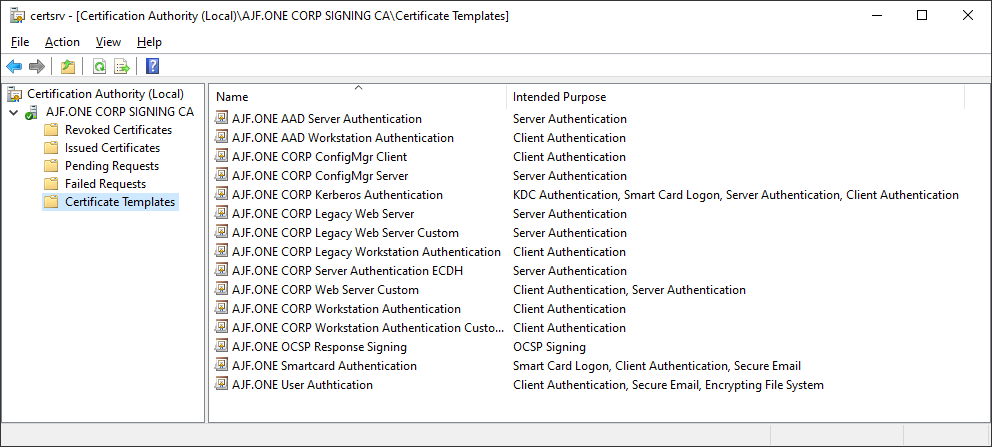
Restart-Service -Name CertSvcUnpublish default templates and publish custom templates
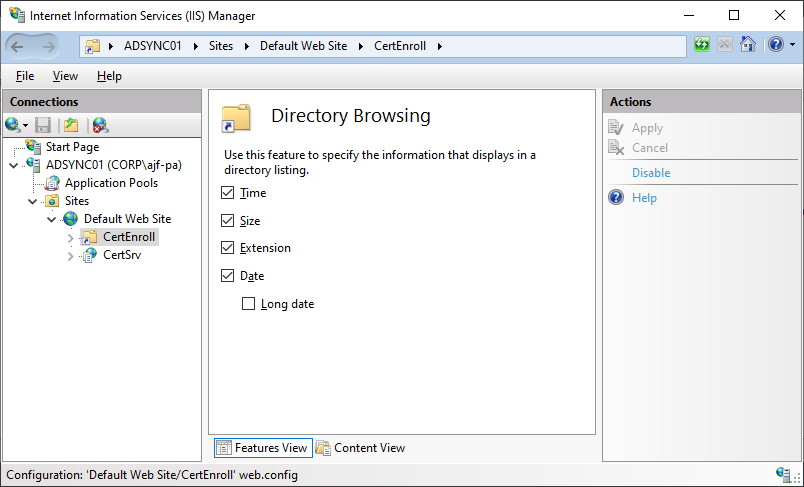
Enable Directory Browsing for CertEnroll directory in IIS
Copy over previous AIA files from old CA (unsure if actually needed, but easy enough to do)
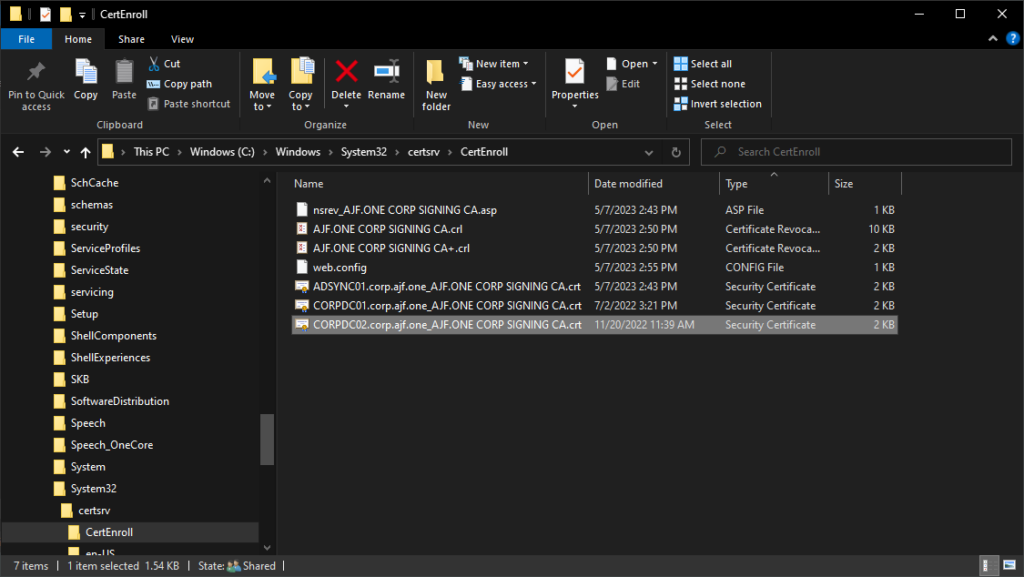
Verify the new CDP can be accessed internally and externally via AAD App Proxy
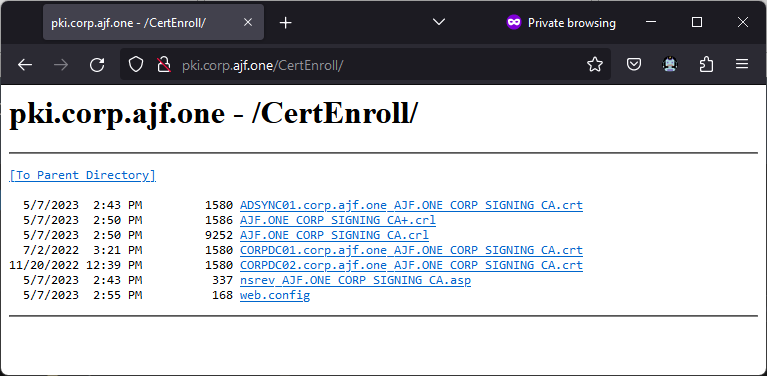
Use pkiview.msc to verify CDP/AIA is valid (note, OCSP will be in an error state until reinstalled)
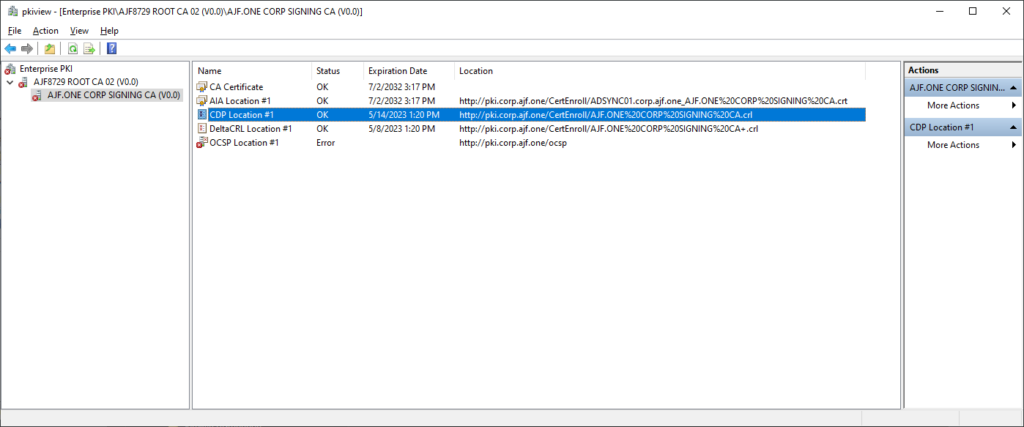
Use certutil from a client to also verify CDP validity
certutil -url http://pki.corp.ajf.one/CertEnroll/AJF.ONE%20CORP%20SIGNING%20CA.crl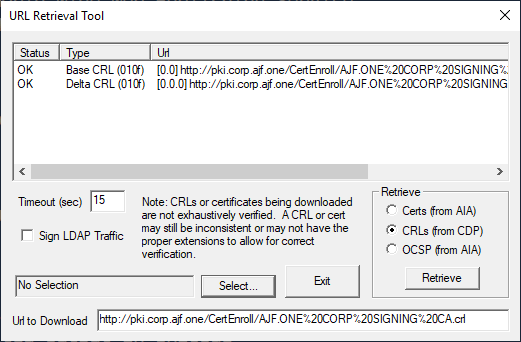
Reinstalling OCSP
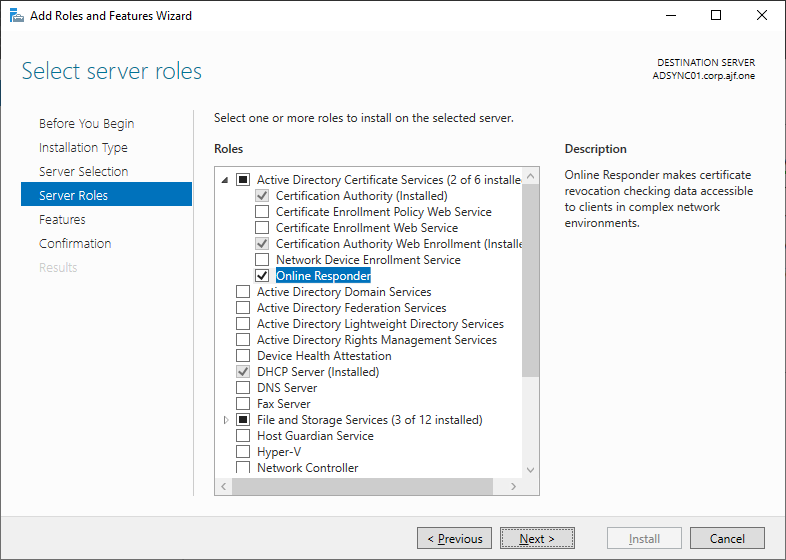
Reconfiguring OCSP
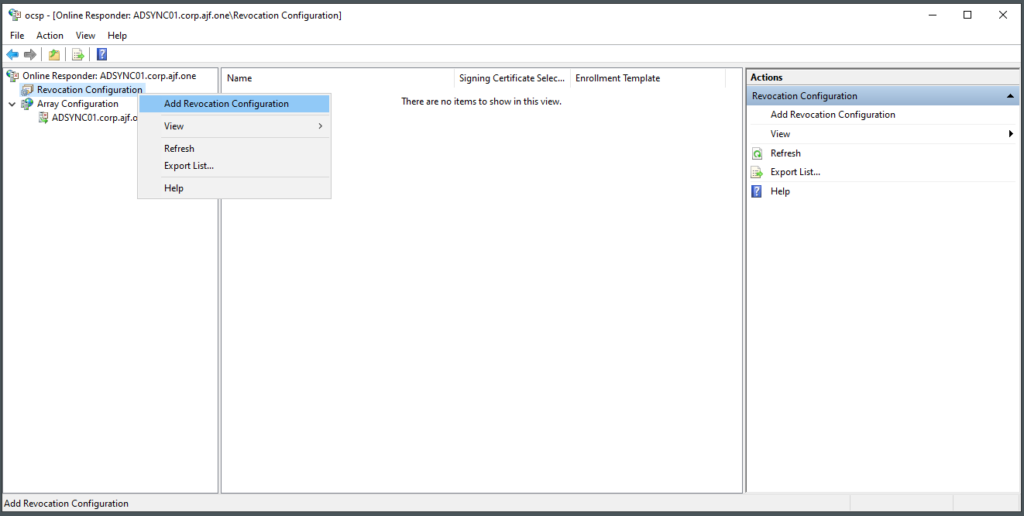
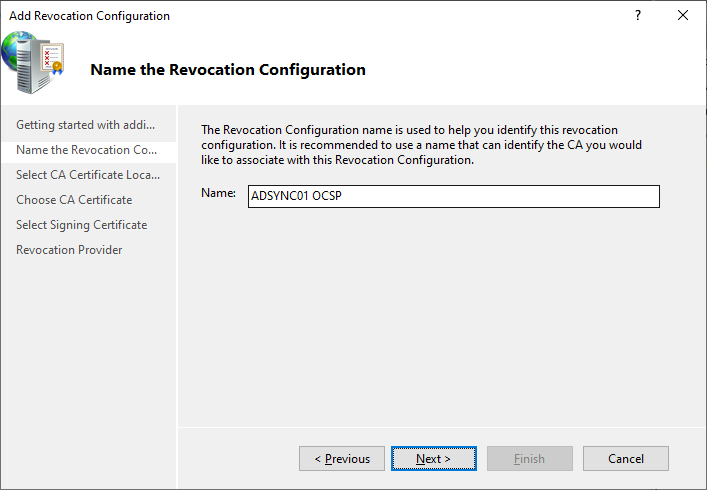
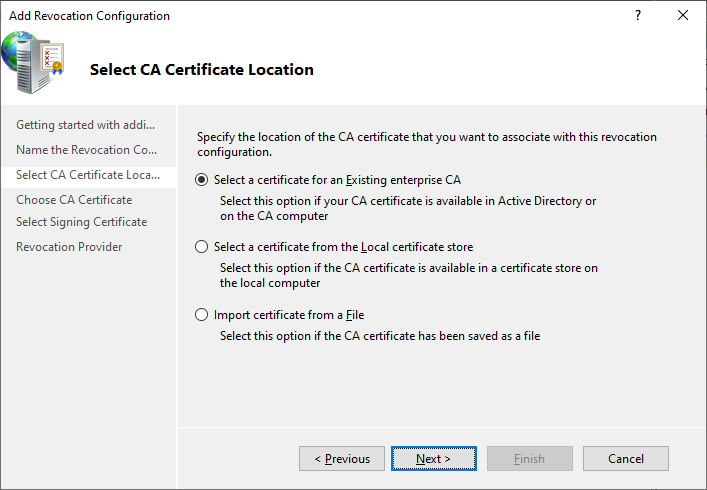
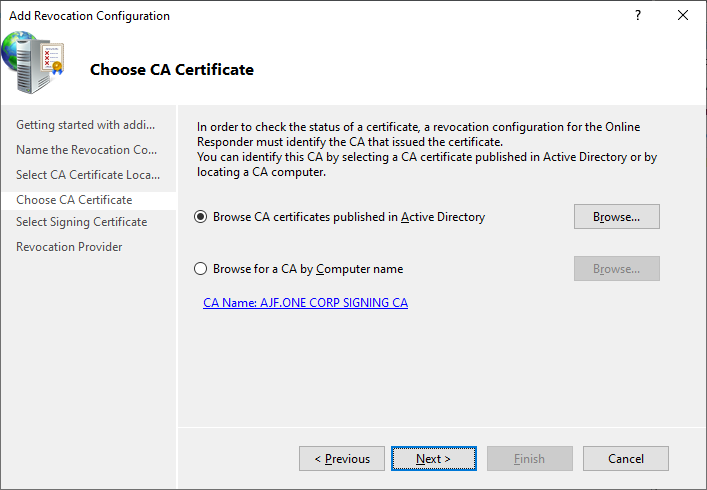
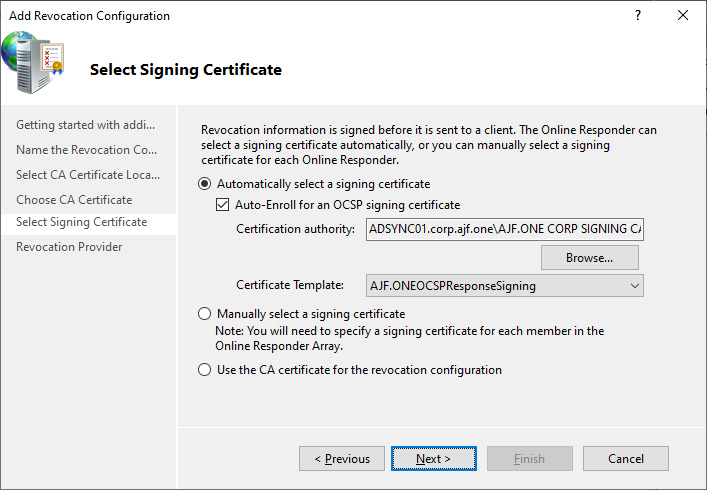
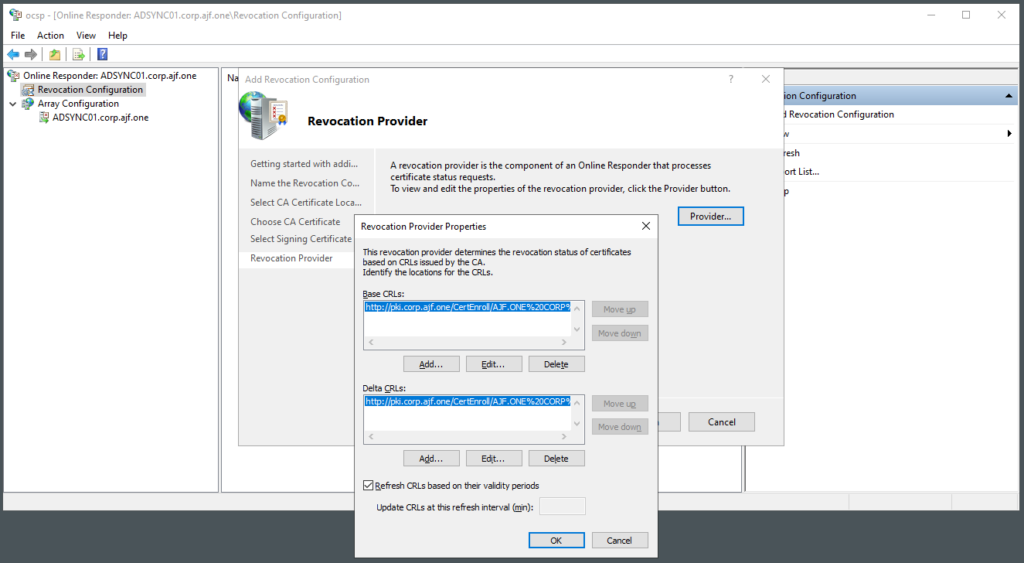
Verify OCSP Configuration
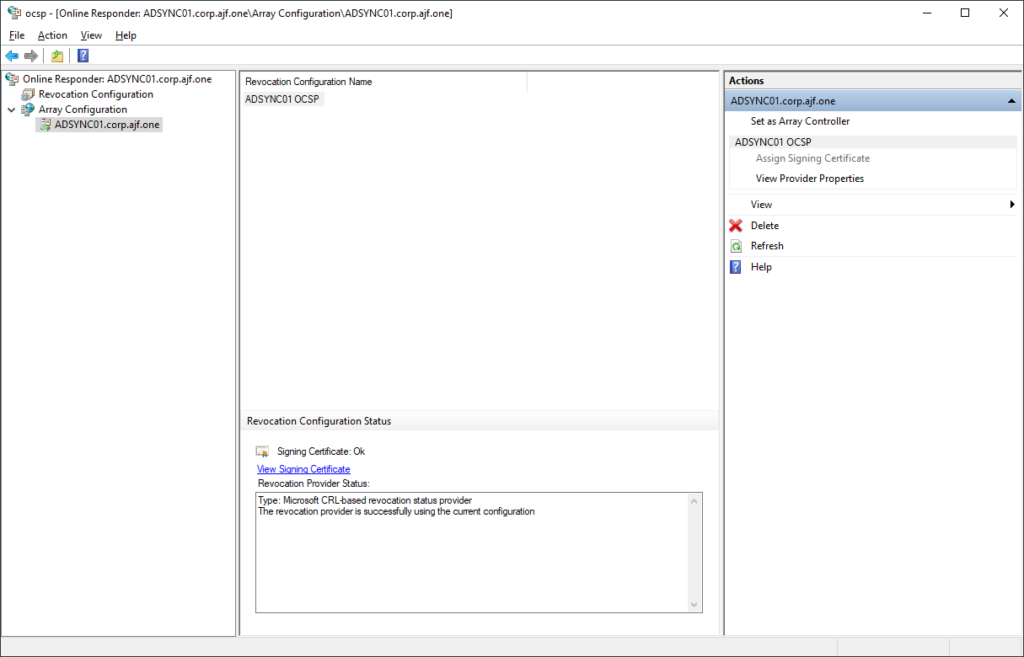
If the OCSP application does not appear in IIS, run the following to recreate it
certutil -vocsprootValidating everything via pkiview.msc
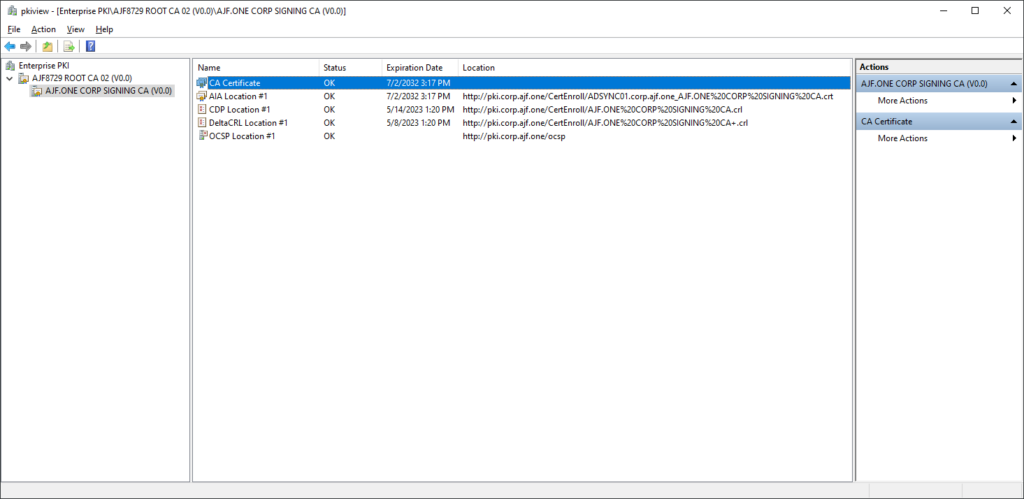
Export a local cert and verify it via OCSP with certutil -url
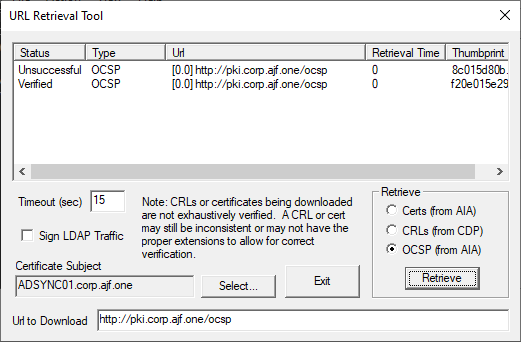
Congratulations! You’re done!


What is the behavior of the existing clients pointing to an existing OCSP responder, but was migrated to a new host? The existing machines pick up the new OCSP responder automatically or is there a manual process for updating them?
In my labs, I use an alias name for my CRL/AIA information, so in migrating the CA to a new host, the alias moves with it, and the OCSP responder continues to function as expected. If it moves to a new name, the CA configuration would need to be updated and new leaf certificated issued to endpoints to utilize the new responder before the old responder could be retired.