Trusted Certificate profiles in Intune are great. Unfortunately, the only certificate stores you can access with these are the Trusted Root and Trusted Intermediate stores. Sometimes, we may need to import a certificate into a different store; Trusted Publishers and Trusted People are two that come to my mind. Luckily, we can easily use a Remediation to import a certificate into any store we want!
2024-01-02 EDIT: I learned that this has always been possible via custom OMA-URI settings as well, thanks Jeroen Burgerhout, neat!
- https://learn.microsoft.com/en-us/windows/client-management/mdm/rootcacertificates-csp
- https://bsky.app/profile/jeroen.burgerhout.org/post/3khuea6bawy2v
Gather Certificate Information
First, let’s gather the needed information to put into our script. For this example, I will be using the WSUS signing certificate used to publish third party updates in my ConfigMgr site. Start by exporting the certificate we want, specifically as a base 64 encoded file:
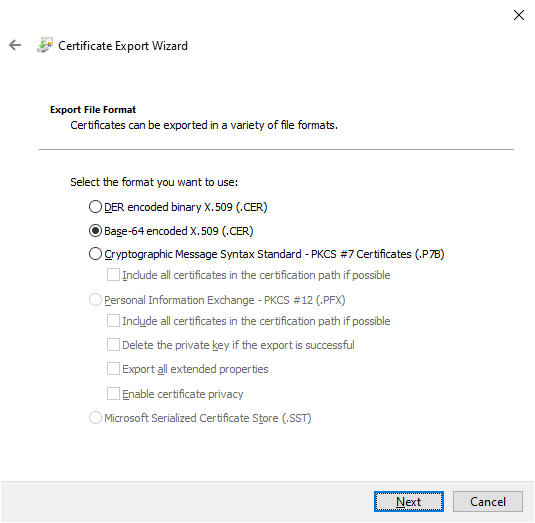
Next, get the thumbprint of the certificate as well; this can easily be done via PowerShell from a device with the certificate already present, otherwise, you can also get it from the exported certificate properties:
PS C:\> gci Cert:\LocalMachine\TrustedPublisher\
PSParentPath: Microsoft.PowerShell.Security\Certificate::LocalMachine\TrustedPublisher
Thumbprint Subject
---------- -------
A053DF291934DCB023A2C2C2A0C9C0B7FFFEC4D7 CN=WSUS Publishers Self-signed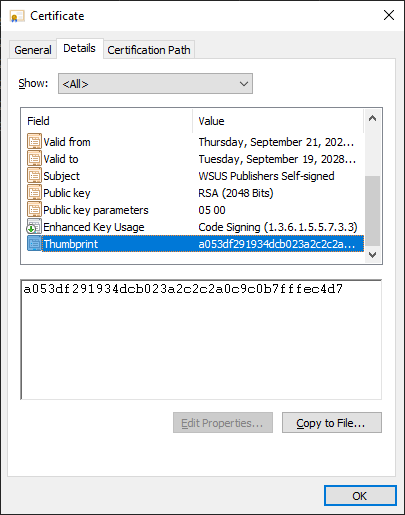
Now that we have all of the information we need, we can combine it into our Remediation scripts:
Detection Script
https://github.com/ajf8729/Toolbox/blob/main/Intune/PR/Import%20Certificate/Detection.ps1
$Thumbprint = 'A053DF291934DCB023A2C2C2A0C9C0B7FFFEC4D7'
$Store = 'TrustedPublisher'
if (Test-Path -Path "Cert:\LocalMachine\$Store\$Thumbprint") {
Write-Output 'Certificate exists'
exit 0
}
else {
Write-Output 'Certificate does not exist'
exit 1
}In the detection script, we will set $Thumbprint to be the value of the expected certificate we are checking for, and $Store to be the name of the certificate store we are checking.
Remediation Script
https://github.com/ajf8729/Toolbox/blob/main/Intune/PR/Import%20Certificate/Remediation.ps1
$Certificate = @'
-----BEGIN CERTIFICATE-----
MIIC7TCCAdWgAwIBAgIQbz8rVazRoKpPqOJB9x1uSTANBgkqhkiG9w0BAQsFADAm
MSQwIgYDVQQDExtXU1VTIFB1Ymxpc2hlcnMgU2VsZi1zaWduZWQwHhcNMjMwOTIx
MTk1NTMxWhcNMjgwOTE5MTk1NTMxWjAmMSQwIgYDVQQDExtXU1VTIFB1Ymxpc2hl
cnMgU2VsZi1zaWduZWQwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDk
+9X8ZcheMK9dV2n0d9xdbaggGJOSaUEJtLHPZBvW4xaU4d1TuELHnMhxj+4JLpno
nimls14hXdJHYRK8BMoM4iKtNl4g0GlCAnv1hvpKBioP5qdXCo6lv+DneCjo2fWR
s7m5IRpXwfnD/P+3AbQP7/4yxcPIjqaKi00VRpRg1JqLkppDc9jLTP55arcyAVAq
meW5Oyanh9y5qZ6mgPK9NgygINUxqHI+9k6OogNZ1x1Jcajr5+T7K45mK7x22Hy6
eTE1YPWBtvlfGuFCP1RBTLxWvUJHxx8kVfPEoklfiy1dUZKBzRf/kmkEe+SnJ034
puk/Syf7VM0HOIexSMUNAgMBAAGjFzAVMBMGA1UdJQQMMAoGCCsGAQUFBwMDMA0G
CSqGSIb3DQEBCwUAA4IBAQC3+7DXPf7taPZbarZig0IfH1zYeIbIr8ImsHU5E3QN
RZXxuFBuXQIUVLNsmigW2HntCDtwDKRi5lGEbvB5fe73gPLdyhEe6vgGmV3H2lYX
VxGr3ZAC9r/Fmk59RtB87iBwUlMxQuxb/mMQIMIAzEiNnuyORZ2Yfbd6ShNwyvUl
swcDodlB2iGCAZ6ktJBk9BiUevfO68LdeYzl4/OEulhzfD8hBzuT9rYF75yoFoNr
gIsli3kszJ62MnroDpkExx47igYIajoWb+/FI7VI242PErI0+3KbaICnd6U9BWA2
a8C5b8oE1zOEq14Y0oPaaiXkIQhAbqY2E+26o86rNi+w
-----END CERTIFICATE-----
'@
$Store = 'TrustedPublisher'
$Filename = (New-Guid).Guid
$Certificate | Out-File -FilePath "$env:TEMP\$Filename.cer"
Import-Certificate -FilePath "$env:TEMP\$Filename.cer" -CertStoreLocation "Cert:\LocalMachine\$Store" | Out-Null
Remove-Item -Path "$env:TEMP\$Filename.cer" -ForceIn the remediation script, we will set the $Certificate here-string to be the base 64 encoded data from the exported certificate file.
Be sure to update the Store name to the correct value in both scripts if using a store other than Trusted Publishers.
This works fairly simply; the detection script will check to see if the certificate exists. If it does not, the remediation script will output the certificate to a temp file, use Import-Certificate to import it to the correct store, and delete the temp file.
Once your scripts are configured, create a Remediation in Intune, upload the scripts, set your assignments, and you’re all set!
Happy New Year! 🥂

