Part 1 of this series will go over the basic configuration of the Windows Firewall via Group Policy on client endpoints, and go in-depth into a few specific topics that will be referenced/reused in later posts.
Overview
In the majority of cases, clients should be able to be secured by allowing outbound traffic by default, blocking inbound traffic by default, and explicitly allowing any necessary inbound traffic for remote management purposes. Except in the cases of specialized software or hardware, there shouldn’t be a need to open any ports on clients that are generally open from anything, i.e., clients shouldn’t be making services available to other endpoints. Let’s start by taking a look at the firewall on a stock Windows 10 installation:
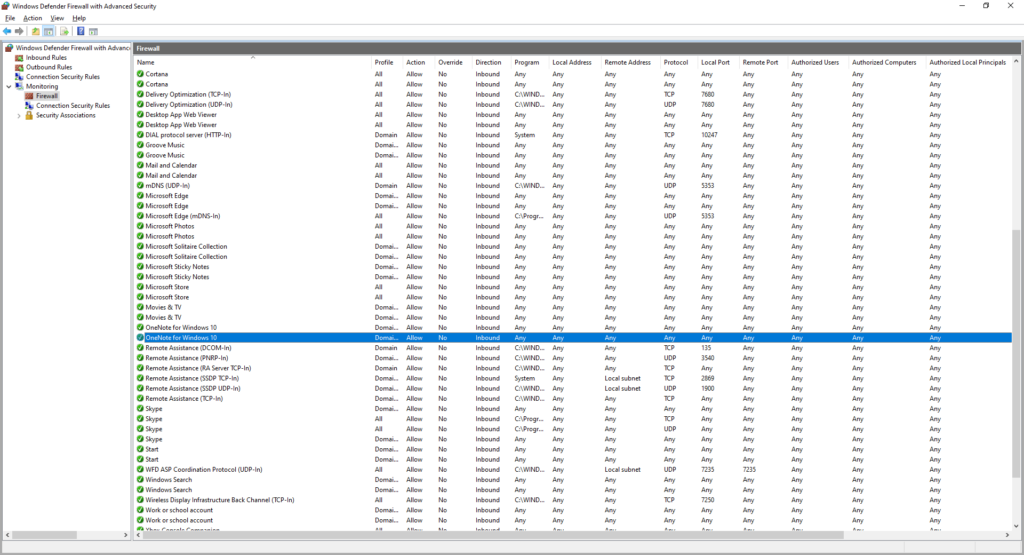
There’s a great deal of rules that come preloaded; but most if not all of them are unnecessary. Most of these are application-specific rules that are created by default.
Basic Client Configuration
To begin, create a new Group Policy Object linked to the top-level client OU, and edit the Windows Firewall section under “Computer Configuration\Policies\Windows Settings\Security Settings”.
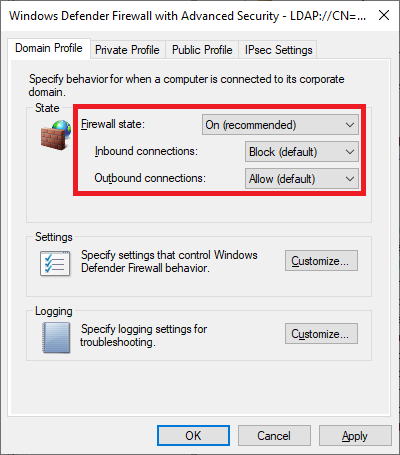
After opening Properties for Windows Firewall, configure each firewall profile to enable the firewall, block inbound connections, and allow outbound connections.
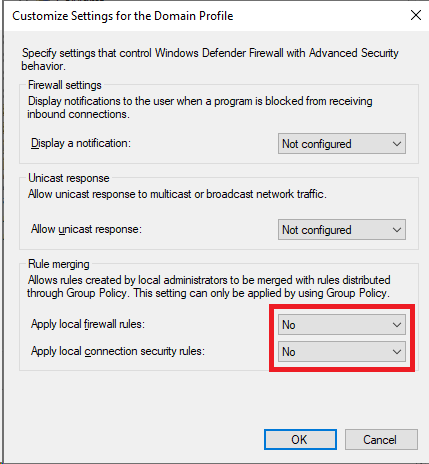
Next, customize the settings for each profile to prevent locally configured rules from applying. This will ensure that all firewall rules must be defined via Group Policy, and prevent rules created locally even by an administrator from applying. These settings can be accessed by clicking “Customize” in the “Settings” section for each profile.
Next, create a new rule via the wizard to allow inbound ICMP echo requests for troubleshooting purposes. Right-click Inbound Rules, click New Rule, and select Custom.
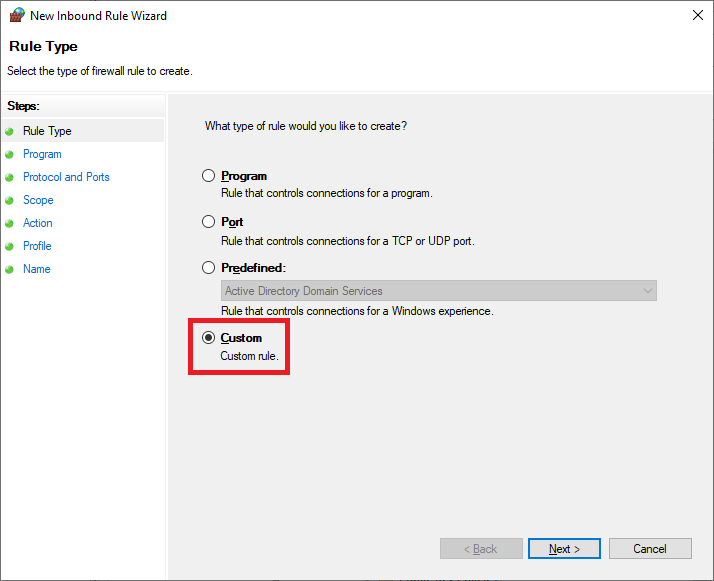
Select All Programs, click Next, select ICMPv4 under Protocol Type, and click Customize. In the customization dialog, select Specific ICMP Types, and then select Echo Request.
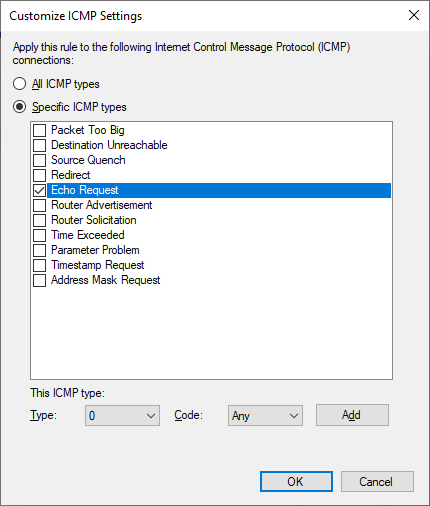
Click OK, then accept the defaults for Scope, Action, and Profile, then give the rule a useful name, such as “Allow Inbound ICMP Echo Request”.
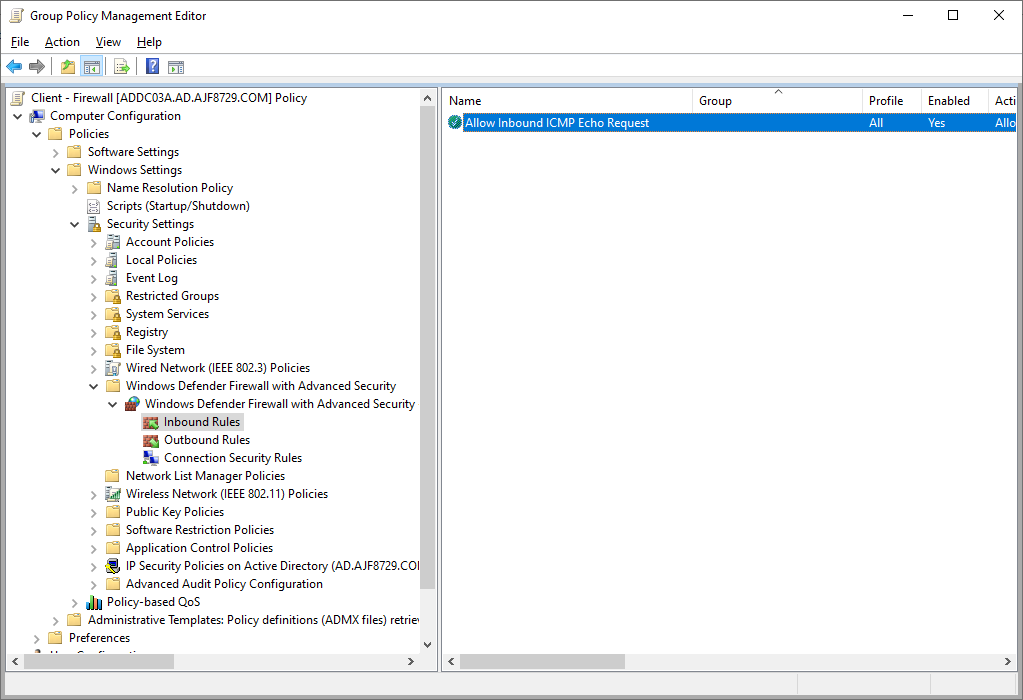
Next, create a rule to allow remote SMB access for remote management purposes. This time, use PowerShell to create the rule directly in the GPO using the New-NetFirewallRule cmdlet, replacing the parameter values below as necessary.
|
1 2 3 4 5 6 7 8 9 10 11 |
$Parameters = @{ 'PolicyStore' = 'ad.domain.tld\Client - Firewall'; 'Name' = 'Allow Inbound SMB from management server'; 'DisplayName' = 'Allow Inbound SMB from management server'; 'Direction' = 'Inbound'; 'RemoteAddress' = '10.20.30.40'; 'LocalPort' = '445'; 'Protocol' = 'TCP' } New-NetFirewallRule @Parameters |
Further documentation for the New-NetFirewallRule cmdlet can be found on the Microsoft Docs site. Using PowerShell can make it much easier/quicker to create many rules, such as additional rules for other remote management purposes, such as WinRM, remote WMI access, etc.
Summary
At this point, the most vulnerable endpoints are now drastically more secure. If a client is compromised, there won’t be any ability for it to pivot to other client endpoints and cause further compromise, nor can local firewall rules be created to provide a “backdoor”.


