Alright, now on to where things get more complicated, WinRM connections to and from Azure AD joined clients. I’m going to use two acronyms throughout this post that I want to define now:
- HAADJ – A Hybrid Azure AD Joined device. For the context of this post, this device could also be a purely AD joined device.
- AADJ – A purely Azure AD Joined, specifically logged into with a hybrid (synced via Azure AD Connect) identity.
There are two scenarios I’ll cover, each with their own nuisances: Azure AD clients as the source, and as the destination. If you’re following along from Part I, I’ve since reverted the existing WinRM firewall rule on my servers to normal, so no IPSec is required.
AADJ -> HAADJ WinRM
From an AADJ client, let’s just try to etsn to a server and specify credentials. Surely it will just work, right? I’ve got Azure AD Connect in place, along with Azure AD Kerberos and Hybrid Cloud Kerberos Trust. I can log in with Windows Hello for Business and successfully access on-premises resources without issue. Well…
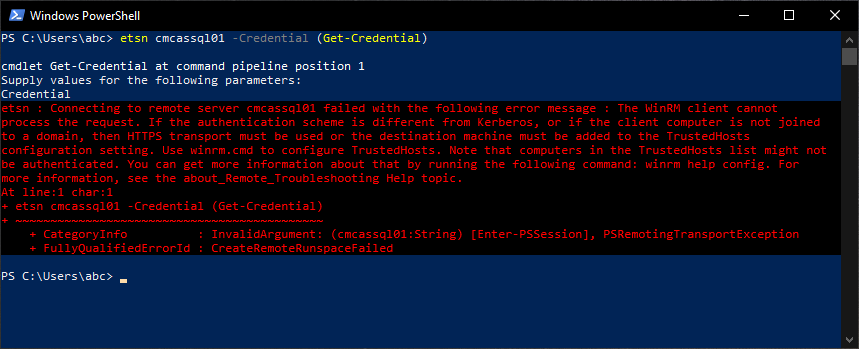
No dice. Since the source client isn’t domain-joined, and we’re attempting to use normal WinRM (not over HTTPS), Kerberos mutual authentication at the device level cannot occur. The source device does not have an identity in AD. I guess we’ll just need to go back to Hybrid devices. Wrong!
We can go about fixing this in two different ways. First, the easy, but less secure route: Trusted Hosts. Let’s configure a Settings Catalog profile in Intune to set some WinRM settings:
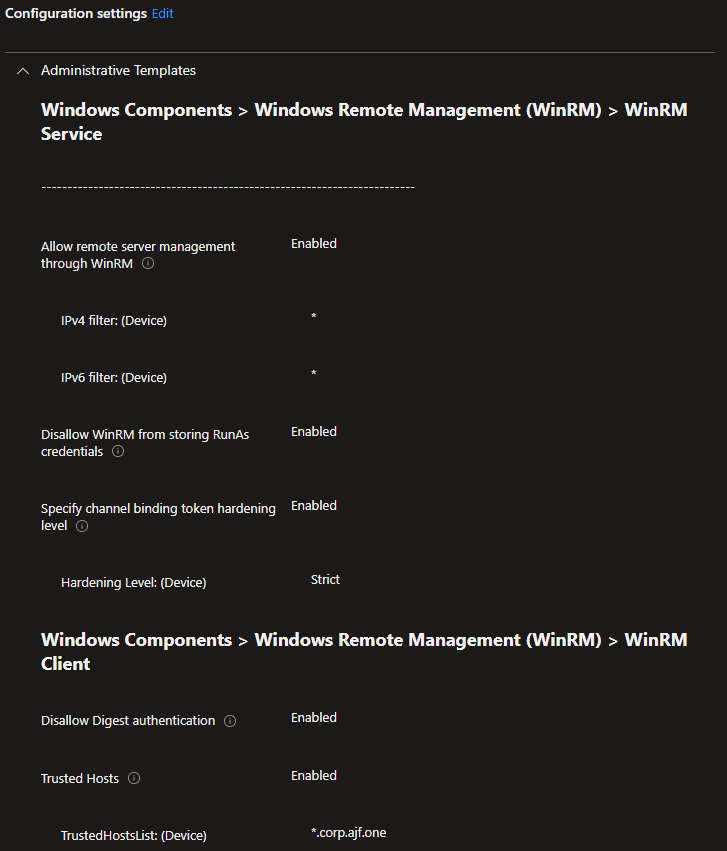
Similar to the policy we created in AD in part I, I’m enabling the settings I desire, while additionally configuring the Trusted Host list to include my wildcarded AD domain name. This configuration will instruct the client to not perform Kerberos mutual authentication at the device level, and allow the connection to succeed for that domain. This does pose a security risk, because if a compromised device can assume the DNS name of a domain client, you can inadvertently send your credentials to it.
We can at least counter this by configuring NTLM authentication restrictions on the client, or by adding the user account being used to the Protected Users group to prevent NTLM authentication and only allow Kerberos authentication. Both of these can be pretty powerful in securing your environment further. For now, we’re going to test this as-is.
If you were to try to run the same command, it will still fail, because we were trying to use the “short” name and letting DNS suffix search order handle things. That won’t fly here, we’ll now need to use the FQDN in order to connect:
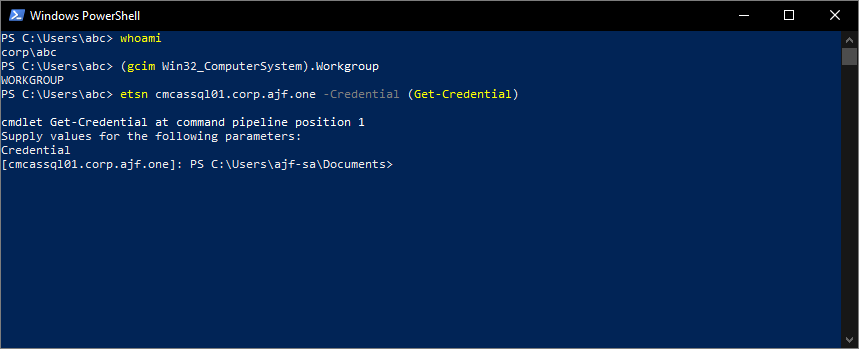
We’re in! But, can we make the connection not rely on Trusted Hosts? Yes, with certificates! Let’s configure WinRM on the server side to accept connections over HTTPS over port 5986. I already have a PKI infrastructure in place (check out Chris Kibble‘s excellent series on PKI here: Standing up a Microsoft Certificate Authority for more guidance), and server authentication certificates enrolled on my servers for securing IIS and SQL, so let’s use that certificate for WinRM as well. Two birds stoned at once, right?
Configuring this isn’t straightforward; it will need to be scripted and deployed via a management tool such as ConfigMgr or Intune. The following is an example script that can configure it; this will need tweaking depending on the environment.
$WCS = Get-CimInstance -ClassName Win32_ComputerSystem
$FQDN="$($WCS.Name).$($WCS.Domain)"
$Thumbprint = (Get-ChildItem -Path Cert:\LocalMachine\My\ |
Where-Object -FilterScript {
$_.EnhancedKeyUsageList -in 'Server Authentication (1.3.6.1.5.5.7.3.1)' -and
$_.Issuer -eq 'CN=AJF.ONE CORP SIGNING CA, DC=corp, DC=ajf, DC=one' -and
$_.Subject -eq "CN=$FQDN"
}).Thumbprint
New-Item -Path WSMan:\LocalHost\Listener -Transport HTTPS -Address * -CertificateThumbPrint $Thumbprint –ForceNext, we need to go back to our GPO and create a rule for inbound TCP 5986, as there’s no builtin rule for it.
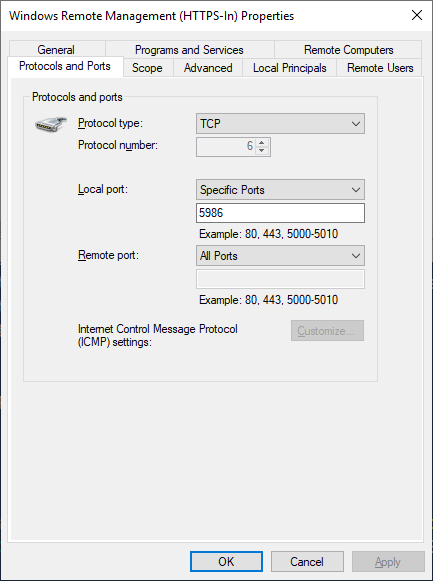
Next, since I’m using an internal PKI, I need to configure trusted certificate profiles for the root and subordinate CAs in Intune, which is a straightforward configuration (see Configure and use PKCS certificates with Intune for further information). Finally, we’ll remove the Trusted Hosts configuration from the WinRM configuration profile we created earlier, and test things out. First, let’s try the short name again, but add the -UseSSL parameter.
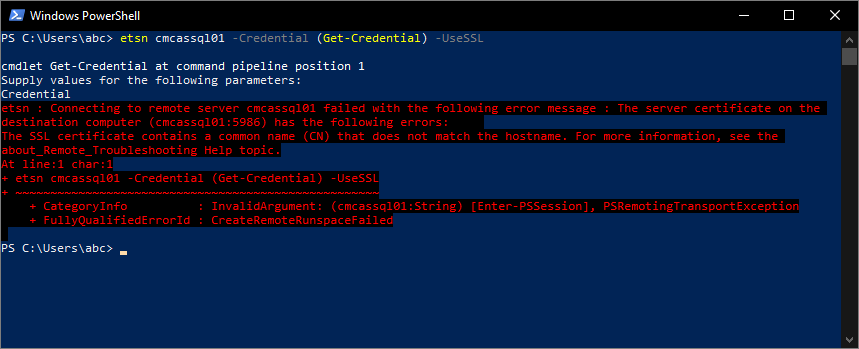
Since the certificate issued to my server only contains the FQDN, name matching fails, and the connection fails. One more time, with the FQDN…
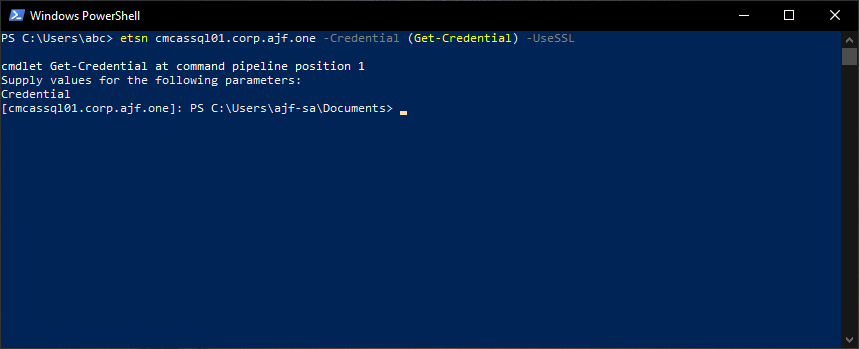
Success! This is a much more secure configuration, as the client is now able to establish a form of trust to validate the server it is connecting to. If a rogue device were to take over the DNS name, and present a certificate with the same name, but an issuer not trusted by the client, connections would fail. As I stated earlier, this methodology will work when connecting to either AD or Hybrid AD joined devices, because the authentication “source of truth” for both types is still AD at the end of the day. Now let’s complicate things further…
HAADJ -> AADJ WinRM
Doing the reverse of the above scenario is a bit trickier. Since we already know utilizing normal WinRM will fail due to Kerberos mutual authentication not being able to complete at the device level, we know we will need to use either Trusted Hosts or certificates.
I’m going to skip configuring Trusted Hosts here, as it is a similar configuration as before, with a caveat that also affects using certificates: DNS registration. Azure AD clients are NOT a member of an AD domain, and they should NOT be registering DNS records in the AD domain DNS zone. To solve this, I’m going to create a new DNS zone named aad.ajf.one and configure my AADJ clients to use that suffix and have records registered there via DHCP. Then, I’m going to use the Intune Certificate Connector to issue server authentication certificates to the AADJ clients via a PKCS profile. In a production environment, I’d most likely opt to use NDES and SCEP as it is a more secure configuration, at the expense of a bit more complexity.
I’ve created a new DNS zone on my domain controller and configured it to support both nonsecure and secure dynamic updates. This is necessary as the client will not be able to authenticate to AD to securely create records, which is another reason to create a new zone.
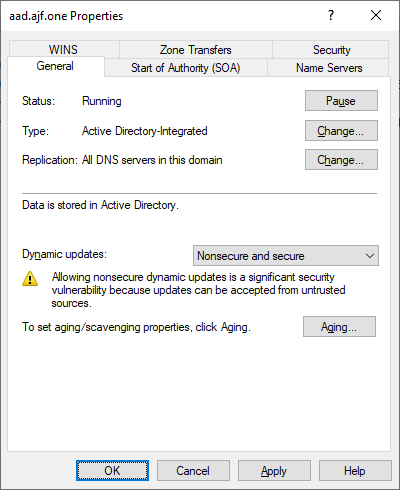
Next, I’ll configure the necessary DHCP and DNS settings to make registration work. For DHCP, I will configure option 15 on the reservation for an AAD client to aad.ajf.one. For DNS, I’ll use a configuration profile in Intune for a few settings.
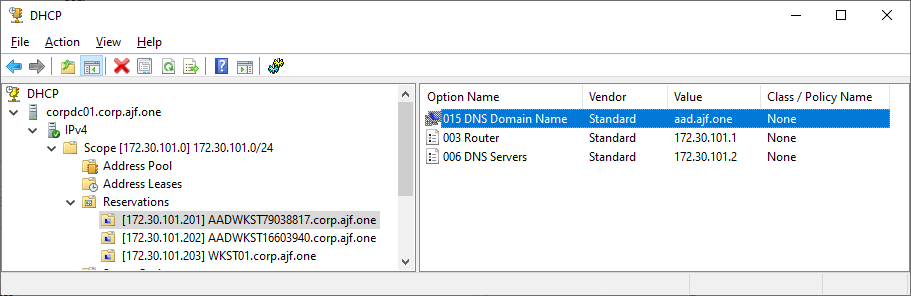
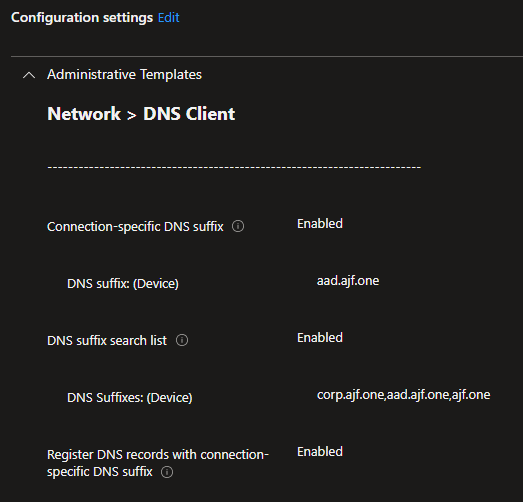
After verifying the profile applied via Intune, I can release/renew DHCP on the AADJ client and confirm the DNS record is created.
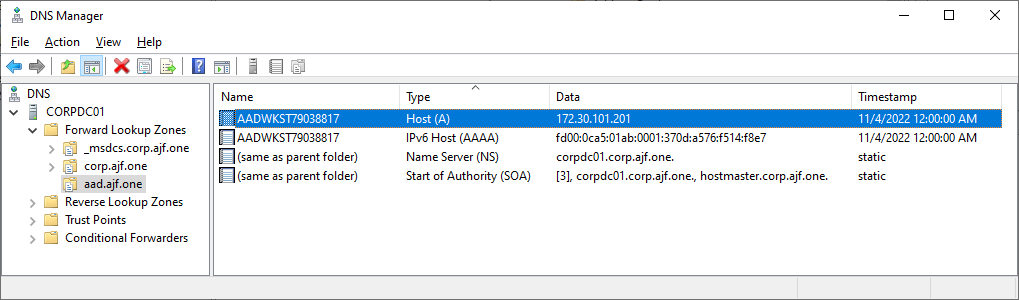
We have a success! Note that I configured the DNS suffix search order as well; this is not strictly necessary for what we are configuring for WinRM, but it’s a good practice. Now, we need to deal with certificate enrollment.
I am already using PKCS to enroll a client authentication certificate, so I just need to set up a new template on my CA and configure a new PKCS profile in Intune and assign it to a group containing my AADJ device.
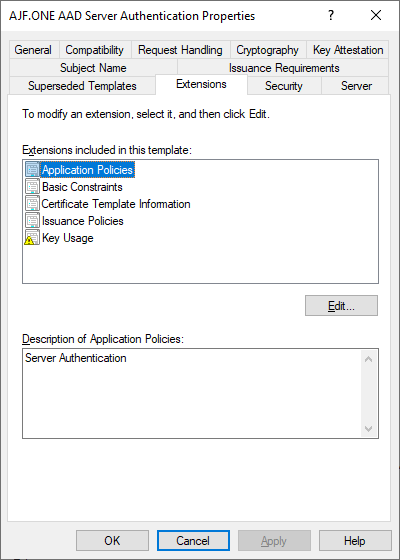
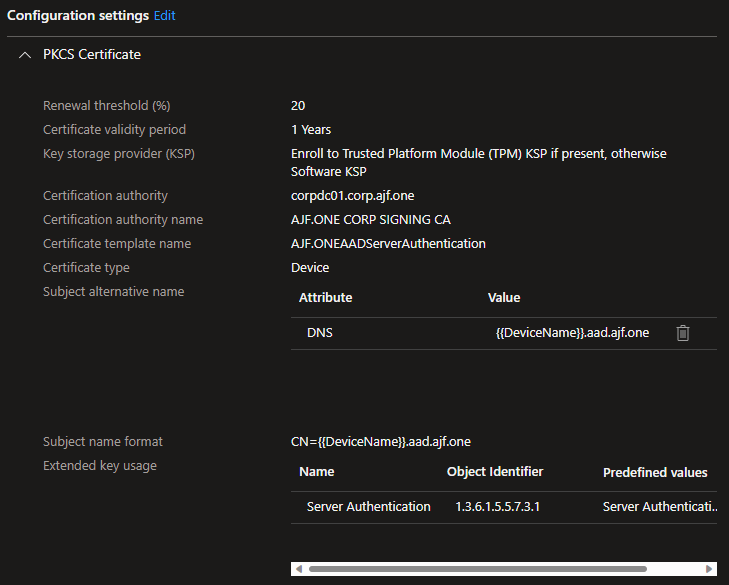
After syncing things up on the client side…
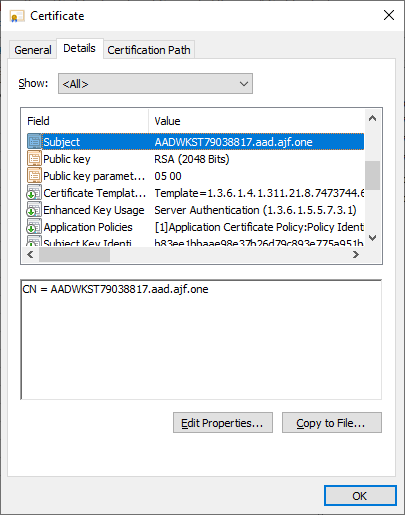
Another success! Now, we can use Intune to configure WinRM and a similar form of the script from part I to configure the WinRM HTTPS listener. This time, we’ll need the script to directly specify the domain name, and we’ll also have it enable and start the WinRM service. Finally, we’ll use a firewall rule profile in Intune to open port 5986.
Set-Service -Name WinRM -StartupType Automatic
Start-Service -Name WinRM
$WCS = Get-CimInstance -ClassName Win32_ComputerSystem
$FQDN="$($WCS.Name).aad.ajf.one"
$Thumbprint = (Get-ChildItem -Path Cert:\LocalMachine\My\ |
Where-Object -FilterScript {
$_.EnhancedKeyUsageList -in 'Server Authentication (1.3.6.1.5.5.7.3.1)' -and
$_.Issuer -eq 'CN=AJF.ONE CORP SIGNING CA, DC=corp, DC=ajf, DC=one' -and
$_.Subject -eq "CN=$FQDN"
}).Thumbprint
New-Item -Path WSMan:\LocalHost\Listener -Transport HTTPS -Address * -CertificateThumbPrint $Thumbprint -Force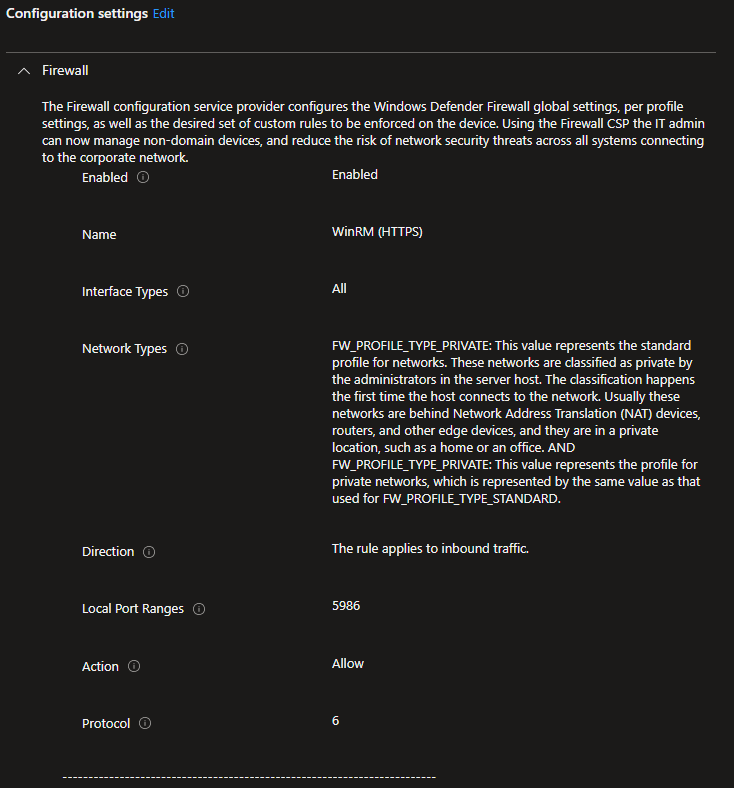
Now, for the moment of truth. Will we be able to successfully connect to an AADJ client from an HAADJ client via WinRM? Well, no, not just yet. What credential do we use? Up to this point, we’ve been using AD credentials, since we were connecting to effectively AD hosts. A pure AADJ device doesn’t know how to use those credentials from a WinRM perspective. You can try all of the forms of username you want (like AzureAD\username@domain.tld for example) but it isn’t going to work. We need to use a local account to finish this off.
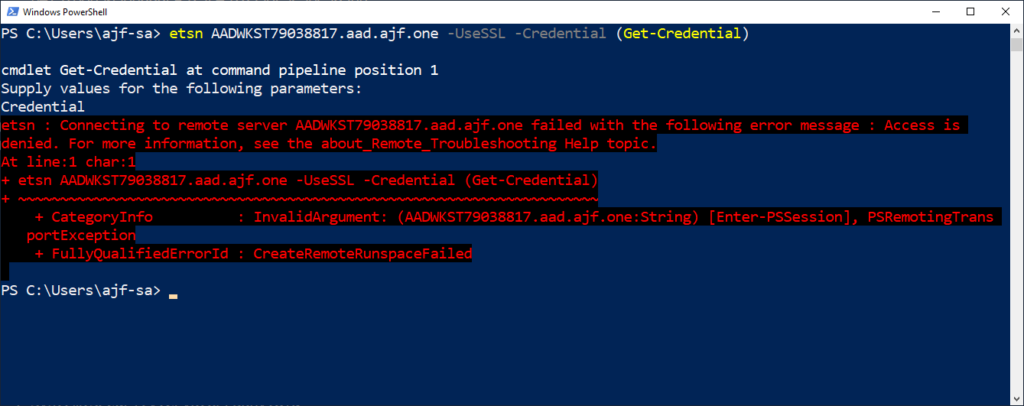
As for making that local account configuration, I leave that up to you. There are various community-based Cloud LAPS solutions out there (such as the one from the MSEndpointMgr folks), as well as LAPS coming soon to Azure AD, so I think this problem will be eventually solved. For my lab demo, I manually set the local Administrator account password and enabled the account.
Finally, the moment you’ve been waiting for:
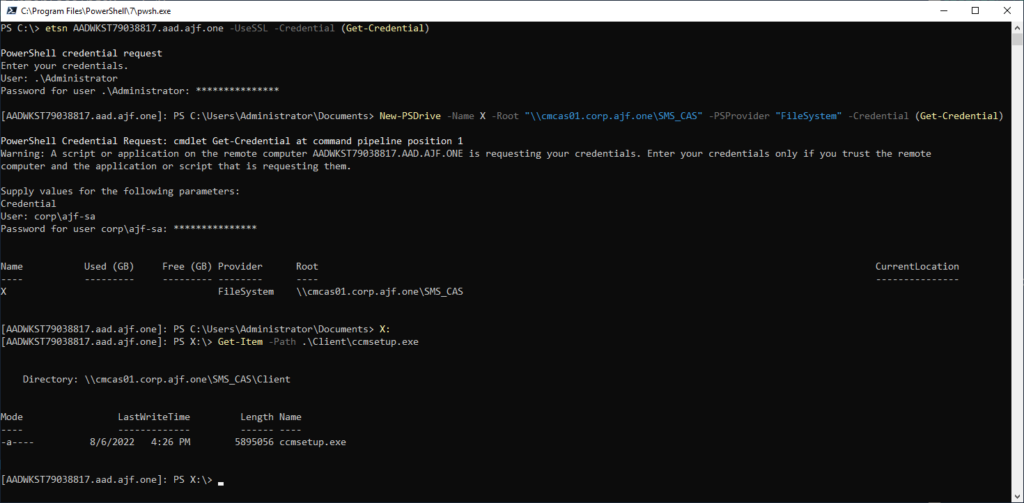
Let’s walk through the above image:
- Connected to an Azure AD joined client via WinRM over HTTPS, secured with a valid and trusted certificate issued via internal PKI.
- Authenticated using the local Administrator account on the remote device.
- Created a PS drive to connect to a share on a server, using an AD domain credential.
- Browsed a file on said share.
Conclusion
- Is making WinRM into Azure AD joined devices possible? Yes
- Can it be done in a secure fashion. Yes
- Is it really necessary? No
- Is it really neat? Absolutely!
In the era of “modern management”, I am a firm believer that it’s time to start treating clients like cattle, the same that we [should] be doing for servers for a while now. Use configuration management platforms such as Intune or ConfigMgr (or both, co-management is great!). Create the policies, scripts, and deployments necessary to get your endpoints in the state you desire, and verify that configuration. These tools have features built-in to ensure that the configuration you specify is in fact configured, and can remediate as needed.
This was a fun experiment, and Johannes owes me a beer 🍺



Hello, i got this working now, thank you for this article. But as soon i assign the windows security baseline, i can’t connect anymore. Do you eventually know which settings i have to change in the Security Baselines to make it work?
Thank you in advance.
I’m not 100% sure, but I will recommend checking out the “Open Intune Baselines” here, https://github.com/SkipToTheEndpoint/OpenIntuneBaseline. There’s lots of folks in the community utilizing them, as the inbox baselines tend to break a lot of things unless you review and test them well before deploying them, removing/changing settings as needed.
On one machine I get:
TEST-WSMan : The server certificate on the destination computer
(T18-PC163CP0.mydomain.local:5986) has the following errors:
Encountered an internal error in the SSL library.
At line:1 char:1
+ TEST-WSMan -ComputerName T18-PC163CP0.mydomain.local -UseSSL
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (T18-PC163CP0.mydomain.local:String) [Test-WSMan], InvalidOpera
tionException
+ FullyQualifiedErrorId : WsManError,Microsoft.WSMan.Management.TestWSManCommand
Works fine from another one, so no big issue, but would be nice what it is
Hmm, not sure off the top of my head. My first guess would be incompatible SChannel settings between the two endpoints, such as no matching cipher suites, hashing algorithms, etc. You can use IISCrypto to check what is current set on both sides and maybe the issue might stick out.
Seems to work from Server 2019 (domain joined) to AAD joined endpoint, but does not work from Windows 11 client (also domain joined or just AAD joined), now tested on few machines with exactly same result
Local WinRM config:
PS C:\Users\lm> winrm e winrm/config/listener
Listener
Address = *
Transport = HTTP
Port = 5985
Hostname
Enabled = true
URLPrefix = wsman
CertificateThumbprint
ListeningOn = 10.10.100.59, 127.0.0.1, ::1, fe80::18ac:c54d:2e69:6ebb%6
Listener
Address = *
Transport = HTTPS
Port = 5986
Hostname
Enabled = true
URLPrefix = wsman
CertificateThumbprint = B90298C5BDD2E6D6A0256799CFCD2000117197E7
ListeningOn = 10.10.100.59, 127.0.0.1, ::1, fe80::18ac:c54d:2e69:6ebb%6
PS C:\Users\localmanager> winrm id
IdentifyResponse
ProtocolVersion = http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd
ProductVendor = Microsoft Corporation
ProductVersion = OS: 10.0.19045 SP: 0.0 Stack: 3.0
SecurityProfiles
SecurityProfileName = http://schemas.dmtf.org/wbem/wsman/1/wsman/secprofile/http/spnego-kerberos, http://schemas.dmtf.org/wbem/wsman/1/wsman/secprofile/https/spnego-kerberos
From another machine (Server 2019 domain joined) works fine (but fails from every Win10/11 client I tried)
PS C:\Users\user> TEST-WSMan -ComputerName T18-PC163CP0.mydomain.local -UseSSL
wsmid : http://schemas.dmtf.org/wbem/wsman/identity/1/wsmanidentity.xsd
ProtocolVersion : http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd
ProductVendor : Microsoft Corporation
ProductVersion : OS: 0.0.0 SP: 0.0 Stack: 3.0
iisCrypt set to Best Practice on BOTH
Very simple “solution” to above issue:
https://learn.microsoft.com/en-us/answers/questions/467673/windows-10-tpm-2-0-client-authentication-in-tls-1
Hi,
about “configure a new PKCS profile in Intune and assign it to a group containing my AADJ device.” part, you just fill up the CA server name, profile… and that’s it?
is it that simple to have an AADJ device with computer certificate from on-prem PKI ??
can you elaborate about this part please
For this most part, yes. Take a look at the PKCS docs for much more detail on the entire configuration – https://learn.microsoft.com/en-us/mem/intune/protect/certificates-pfx-configure.
I’d also recommend looking at Intune Suite and Cloud PKI now that it is available, as it is a much easier route to enroll certificates using SCEP – https://learn.microsoft.com/en-us/mem/intune/protect/microsoft-cloud-pki-overview.
good!!!
For winrm from HAADJ to AAJ device, do they both have to be on same network? I.e. what if AAJ device out there on internet, as long as they both part of same AAD domain, good to go?
If relying on using the DNS name of the AADJ endpoint to connect to, the device would need to be on the same network. I wouldn’t expect anyone to be opening WinRM on clients in the Private firewall profile, or have them be internet-accessible, and if the device is at home, it’s likely going to be behind a NAT anyway.