2023-03-14 Update: The following post is now considered deprecated, as the updates released on 2023-03-14 offer a much better solution that does not involve workarounds. Please see KB5020276—Netjoin: Domain join hardening changes for more information (scroll down to the “March 14, 2023 behavior” section).
NOTE: This is 100% a workaround to a security bug/fix. I hope to have a second post out soon that has a better solution, but it may involve a number of things, including searching for an existing computer object, saving it’s OU and group membership, and deleting it. It may further also go into fixing the root issue of an overprivileged domain join account that has owner permissions to many computer objects.
(Additionally, if you move to 100% Azure AD join, this problem no longer exists 😁)
As part of the 2022-10 cumulative update for all supported operating systems, a change was made to resolve a security vulnerability regarding computer account reuse during domain join. More details can be found here: KB5020276 – Netjoin: Domain join hardening changes.
Note that these changes are specifically client-side changes; the additional checks occur client-side when domain join is performed. If your base WIM(s) do not have the 2022-10 CU installed, this will not be an issue.
In environments where tools like ConfigMgr are used for imaging devices, this may pose a problem, if it is expected that computer objects will be reused, and these computer objects may not be owned by the domain join account (e.g. computer objects that were pre-staged by an IT tech, reusing an object that was initially manually joined, etc.).
In my testing, I found a quick workaround, and have ideas for a better solution (see note at top and bottom of post).
Workaround
The workaround for this is to create a new registry value in the OS before domain join occurs and remove it after.
New-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Control\Lsa\ -Name NetJoinLegacyAccountReuse -PropertyType DWORD -Value 1
The above registry setting will enable “legacy” account reuse to function. In order to utilize this method, you may need to change how domain join is handled in your task sequence.
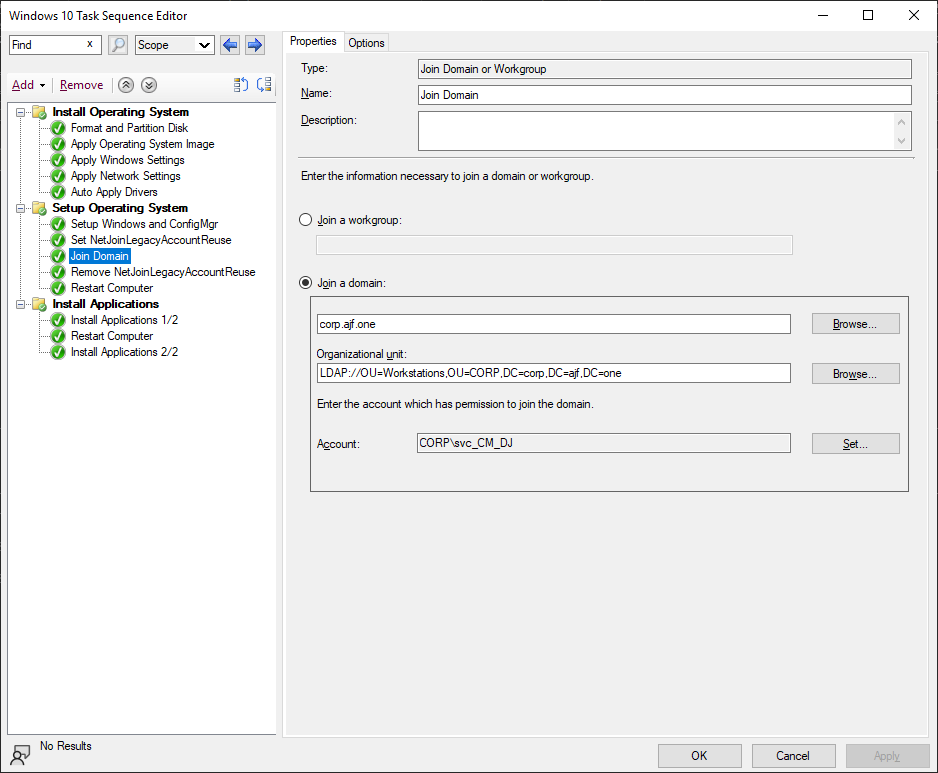
Before I made the above changes, I was initially using the “Apply Network Settings” step to set the domain join information, which would normally get saved to an unattend file in the new OS to be applied later. Since we need to get into the new OS to apply the registry setting, I changed this to join a workgroup instead, and added a few steps after “Setup Windows and ConfigMgr” to do the following:
- “Run PowerShell Script” step to create the registry value
New-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Control\Lsa\ -Name NetJoinLegacyAccountReuse -PropertyType DWORD -Value 1 - “Join Domain or Workgroup” step to join the domain
- “Run PowerShell Script” step to remove the registry value
Remove-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Control\Lsa\ -Name NetJoinLegacyAccountReuse
NOTE: This is 100% a workaround to a security bug/fix. I hope to have a second post out soon that has a better solution, but it may involve a number of things, including searching for an existing computer object, saving it’s OU and group membership, and deleting it. It may further also go into fixing the root issue of an overprivileged domain join account that has owner permissions to many computer objects.

I have applied the GPO on all domain controllers, but same issue, i can’t use another user, i have to use the owner of the object, unfortunately a lot of users used to join the machine, any idea?
Who/what did you configure as “trusted owners” in the GPO? Those are the accounts that would be allowed to reuse the computer object, provided they also already have the necessary delegated rights to that location in the domain. It’s been quite a while since I’ve revisited this, but the update from March 2023 in the KB has more information https://support.microsoft.com/en-us/topic/kb5020276-netjoin-domain-join-hardening-changes-2b65a0f3-1f4c-42ef-ac0f-1caaf421baf8.
Thanks this works 100%.
If you need to run this in WinPE before Domain Join / first boot after applying image to disk.
After your Apply OS to Disk and Apply Windows Settings steps, but Before Domain Join and Setup Windows and Configuration Manager (and a reboot after)
In WinPE
Run Command Line:
reg.exe load HKLM\Temp %OSDTargetSystemDrive%\Windows\system32\config\system
reg.exe add “HKLM\Temp\ControlSet001\Control\LSA” /v NetJoinLegacyAccountReuse /t REG_DWORD /d 1 /f
reg.exe unload HKLM\Temp
Do your Domain Join / Network Settings step
Setup Windows and Configuration Manager
Reboot
Run Command Line:
reg.exe add “HKLM\System\CurrentControlSet\Control\LSA” /v NetJoinLegacyAccountReuse /t REG_DWORD /d 0 /f
Nice one Anthony. Unfortunately I only found this post too late after devising the same solution from first principles for MDT, after trying several times and failing with Reg.exe!
Can confirm this solution works on MDT (assumes that the Registry Key does NOT pre-exist on image, as no check is made) – it’s basically the same as yours but implemented from Run Command Line (mainly from habit because we’ve had issues with Powershell in the WinPE environment), so maybe worth noting this alternative approach (always good to make sure Windows Powershell is added as feature in the MDT WinPE environment too for flexibility in and out of the WinPE environment – we use this for TPM checks before OS install).
Immediately before the Post Install phase of the Task Sequence, add a Run Command Line –
Name – Enable Legacy Owner Domain Join
Description – Adds NetJoinLegacyAccountReuse value from Registry (before Domain Join, requires Restart Computer before State Restore) – see KB5020276. Set Success Codes to 0 in Options.
Command Line – powershell.exe -command “New-ItemProperty -Path ‘HKLM:\System\CurrentControlSet\Control\LSA’ -PropertyType ‘DWord’ -Name ‘NetJoinLegacyAccountReuse’ -Value ‘1’”
Start In – Can be left blank
Under Options put Success Code 0, and make sure Continue on Error box is unticked
Immediately after State Restore phase, ensure there is a Restart Computer task, followed by a Run Command Line –
Name – Disable Legacy Owner Domain Join
Description – Removes NetJoinLegacyAccountReuse value from Registry for security (after Domain Join) – see KB5020276. Set Success Codes to 0 in Options.
Command Line – powershell.exe -command “Remove-ItemProperty -Path ‘HKLM:\System\CurrentControlSet\Control\LSA’ -Name ‘NetJoinLegacyAccountReuse'”
Start In – Can be left blank
Under Options put Success Code 0, and make sure Continue on Error box is unticked
Actually made an error on the above after all that –
Enable Legacy Owner Domain Join should come immediately AFTER Post Install, not before, and should be followed by an extra Restart Computer, otherwise it will not take effect.
Thankyou thankyou thankyou !!!